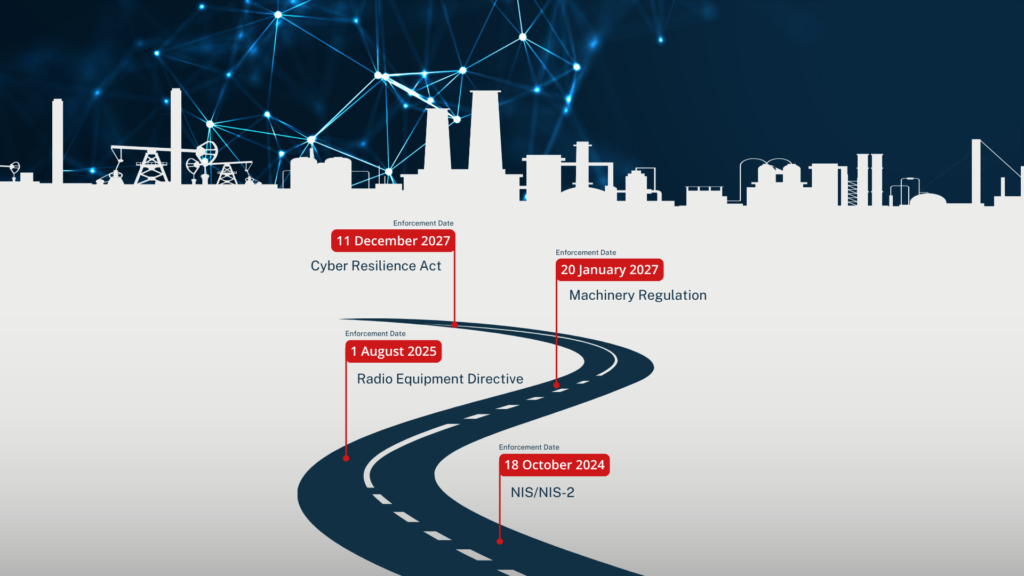
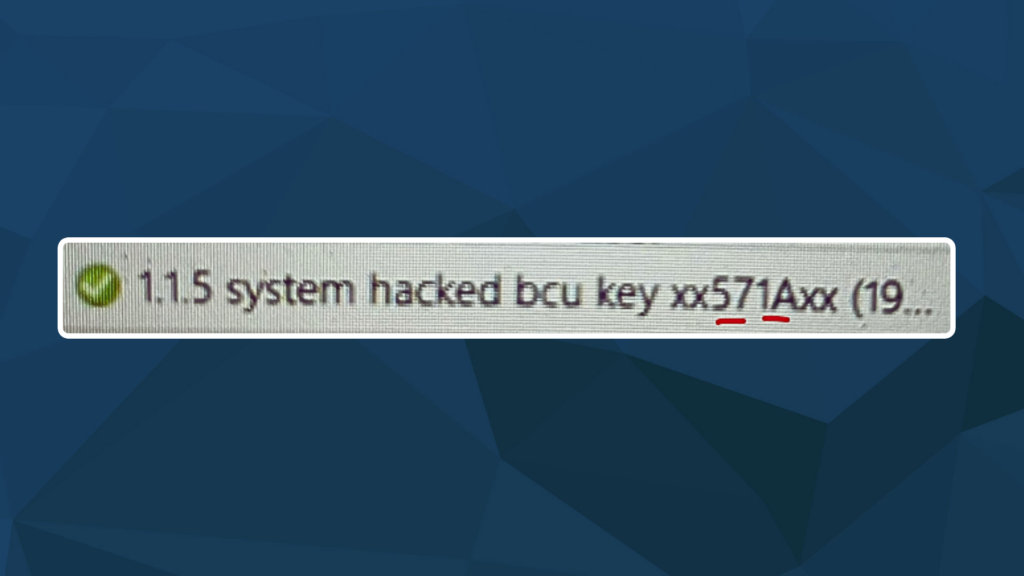
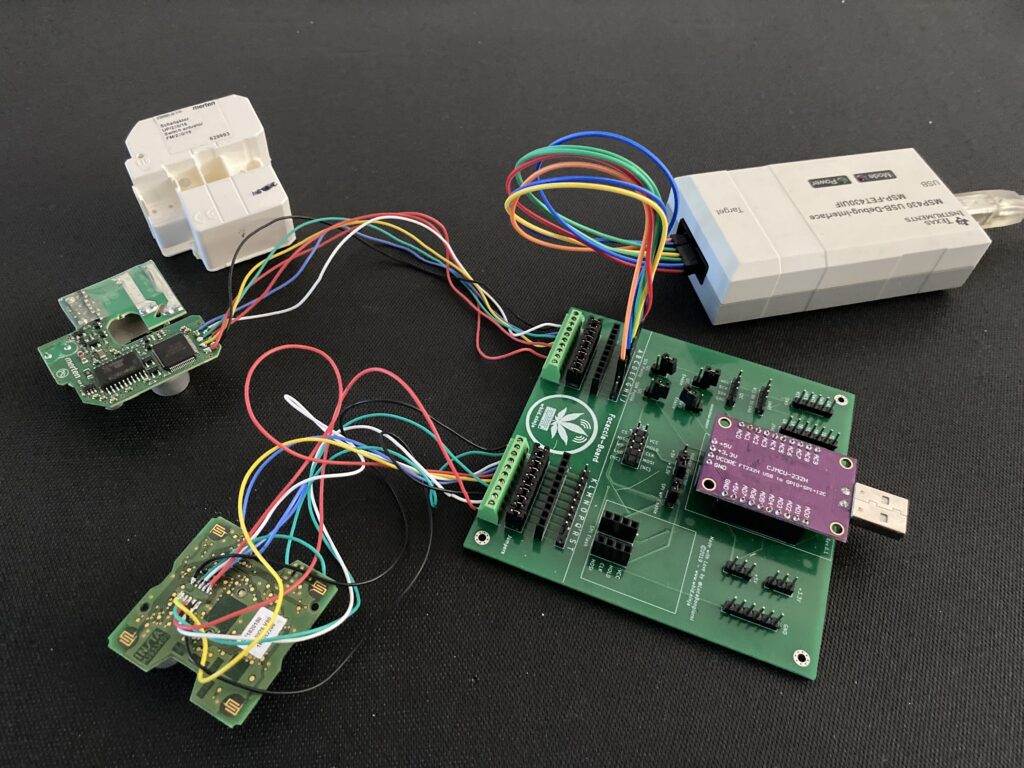
Breaching the OT Perimeter: Authentication Bypass in Claroty Secure Remote Access (CVE-2025-54603)
![]()


Remote access solutions represent one of the most critical attack vectors in OT environments. While…
Iris Wiesinger14. October 2025