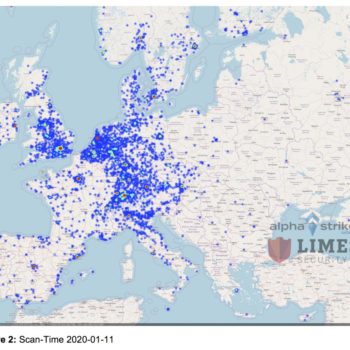
Since 11.01.2020, Alpha Strike Labs of Limes Security GmbH has been performing scans for vulnerable Citrix systems with the vulnerability CVE-2019-19781, which according to current media reports and Twitter comments is already being actively exploited. For scan acquisition, they use the DCS scan network with over 1000 different search nodes [1], which was presented at CCCamp 2019.
A chronological analysis shows that Germany, Switzerland and the Netherlands patched about 85-90% of the Citrix servers that were originally vulnerable on January 21, 2020. Other countries such as China, France and the USA, on the other hand, only achieve a patch rate of 24-56%. On 11.01. there were 49,492 vulnerable Cirtix servers worldwide and on 21.01. there were still 18,620 vulnerable systems.
In Germany, about 24 hours after the Citrix patch was made available, “only” about 800 and in Austria 137 Citrix servers freely accessible from the Internet were affected by the vulnerability.
While 171 clinics and hospitals were still affected at the first scan time in Germany, Austria and Switzerland (DACH region) on 11.01.2020. About 5 days later there were only 31 Citrix instances and another 5 days later only 6 vulnerable systems. However, more than 140 energy suppliers such as public utilities were also affected at the first scan time. At the current point in time (21.01.2020), there are still 21 utilities that have a vulnerable Citrix service.
The public sector, which includes above all the state and federal authorities, also poses a major problem. Here 212 servers were affected on 11.01. and currently only 21 servers were affected. If one takes into account that the first scan was carried out about 3 weeks after the vulnerability became known in mid-December, this shows that the public administration in the DACH region also has some catching up to do in the area of patch or security management.
Searching for traces
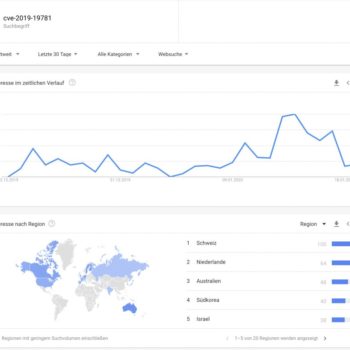
However, the analyses show large differences between countries in terms of patch time. It is very difficult to investigate the causes of this. However, if you look at the countries with Google search queries for the Citrix vulnerability with CVE number “cve-2019-19781”, you can immediately see that the countries with the highest patch level of 90%, Switzerland and the Netherlands, are also the countries with the most search queries for this vulnerability.
Furthermore, it can quickly be seen that from 13.01.2020 onwards, the interest of Google users in the vulnerability has increased significantly. At the same time, the scan data shows that after 13.01.20, the protection of the systems has also increased considerably. This is certainly also connected with the increased media coverage.
Conclusion
It is a good sign that many systems no longer have this vulnerability, but it is also frightening how long it takes to apply the patch or hotfix to the operators of these systems worldwide. The Limes Security team offers more information about this case and how to react quickly – contact us!