During a security assessment for a customer, we discovered five vulnerabilities in Siemens Spectrum Power 4 – a widely deployed SCADA and Energy Management System used by transmission and distribution system operators worldwide. The vulnerabilities enable both local privilege escalation and remote code execution as an application administrator.
First: Siemens has meanwhile released V4.70 SP12 Update 2 addressing all issues. Operators running affected versions should apply the update following Siemens’ guidance.
Discovered Vulnerabilities
CVSS v4.0 Score
Remote command execution via network–accessible UI
CVSS v4.0 Score
Local privilege escalation via debug interface
CVSS v4.0 Score
Local privilege escalation via binary misconfiguration
CVSS v4.0 Score
Credential extraction from world–readable file
CVSS v4.0 Score
Local database manipulation
We are withholding detailed exploitation steps as many operators are still in the process of applying mitigations. However, we can share the general attack pattern for CVE–2024–32011.
Attack Pattern: Kiosk Escape with a Twist
Spectrum Power 4 provides users with a SCADA client to interact with grid management applications on the server. Like other SCADA systems, it uses X11 for graphical rendering–but critically, these sessions render server–side rather than on the client.
From the SCADA user interface, operators can launch various helper applications such as PDF viewers or editors. Some of these applications provide functionality to browse the local filesystem or spawn external programs. An attacker abusing this can escape the intended application boundary – for instance, opening a file browser dialog, navigating to a terminal emulator, or leveraging an application like gvim – to execute shell commands.
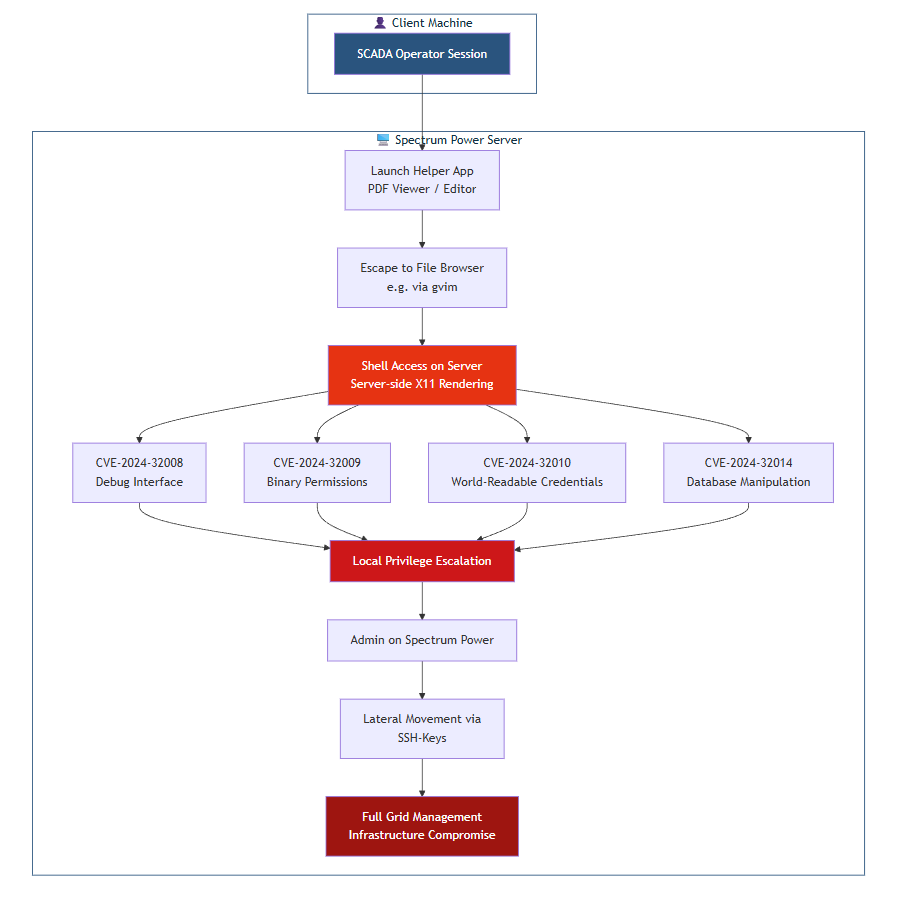
The key issue: because of the server–side X11 architecture, this shell access lands directly on the Spectrum Power server itself, not on the user’s client machine.
From this initial foothold, an attacker can chain the local privilege escalation vulnerabilities (CVE–2024–32008, CVE–2024–32009, or CVE–2024–32010) to achieve full administrative control of the server. Given the interconnected nature of Spectrum Power deployments, this can enable lateral movement across the entire grid management infrastructure.
About Spectrum Power 4
Spectrum Power is Siemens’ grid management platform providing SCADA, energy management, and distribution management capabilities. According to Siemens, it is “the globally leading power grid management software system”. The current generation, Spectrum Power 7, is deployed in over 1,300 control centers across 90 countries.
CISA classifies Spectrum Power deployments within critical infrastructure sectors including Energy, Chemical, Critical Manufacturing, Food and Agriculture, and Water and Wastewater Systems (ICSA-19-099-02).
Legacy, but still in production
Spectrum Power 4 is the predecessor to the current Spectrum Power 7 product line. While Siemens actively markets SP7 for new deployments – including a recent major contract with DB Energie for the German railway grid – many SP4 installations remain in production worldwide.
This is typical for critical infrastructure. SCADA and EMS upgrades are complex multi-year projects involving:
- 24/7 availability requirements – grids cannot go offline for migrations
- Regulatory requirements– new systems require extensive validation
- Integration dependencies – connections to RTUs, historians, market systems, and third-party tools
- Budget cycles – capital expenditure for control system upgrades competes with other grid investments
The result is a long tail of legacy systems running in production, often for a decade or more beyond their intended lifecycle. Security research on these systems remains critical–operators need vulnerability information and patches regardless of whether the product is still actively sold.
This discovery highlights why regular security assessments of SCADA and EMS products remain essential.




