How Drozer can collect data from your installed apps
In recent years, the use of mobile devices such as smartphones and tablets has increased dramatically. Apps have become a fixed part of our everyday life. Unfortunately, it is often overlooked that these apps require the same IT security as traditional desktop applications or websites.
A mistake that often occurs during development is that security features are implemented in the app but are not checked on the server afterwards. An app always runs on a user’s end device and hackers can attack the app directly. This results in many attack surfaces. The communication between the app and the server could be interrupted. But also, internal data of the app can be extracted from the mobile device and harmful modifications can be made. Exported interfaces can also be opened if they do not have enough protective measures.
Drozer on a mission to collect data
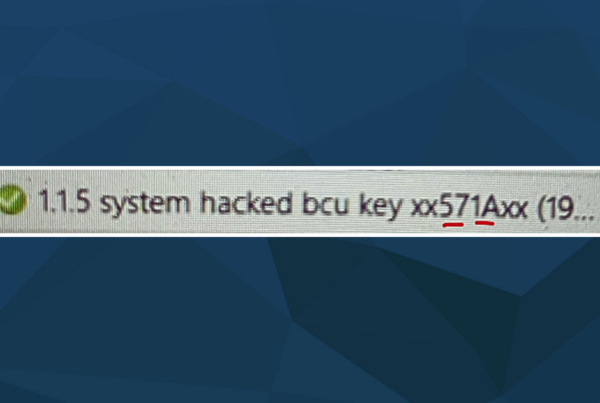
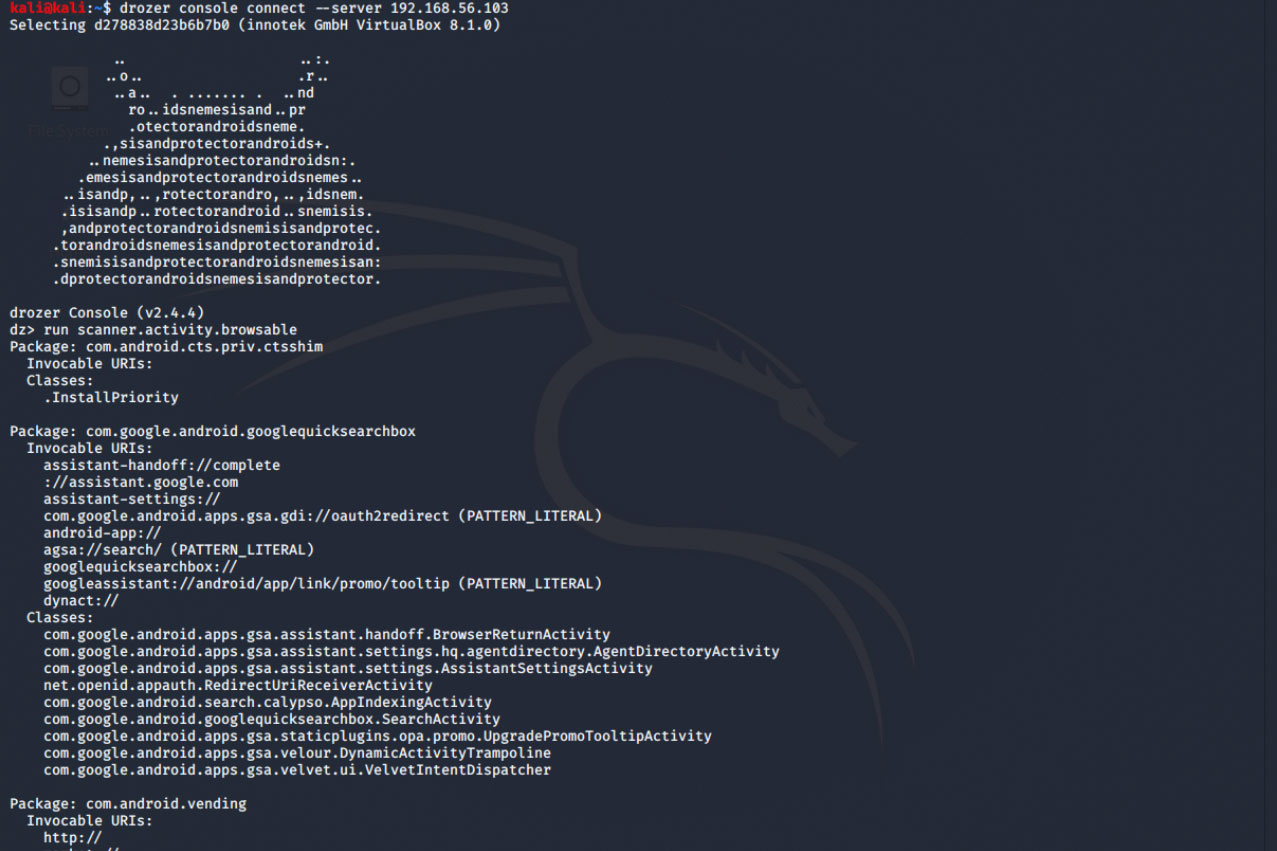
A well-known tool for testing and exploiting vulnerabilities on Android devices is Drozer. If the Drozer agent is installed on a smartphone, an attacker can connect to it and siphon off information about the device. Drozer can impersonate a native Android application, communicate with the Dalvik virtual machine responsible for running apps on Android or collect information about the operating system. Additionally, it allows to retrieve information about installed apps, for example from the manifest.xml file. The tool can not only collect data, but also start activities itself – of particular interest are exposed interfaces such as activities, broadcast receivers, content providers and services. If no sufficient access rights were set for the mentioned interfaces, Drozer can use them to read internal application data.
The average consumer will not voluntarily install Drozer on his smartphone, but it is usually not necessary. Drozer can be delivered as part of a fake app, in order to install itself unnoticed on the device, in addition it does not even need root rights for its functionality. Therefore, apps should only be obtained from trusted sources such as the Play Store or, for iPhones, from the AppStore.
Limes recommends:
If you develop apps yourself and are not sure how much information a Drozer agent can steal from your application, Limes offers security penetration tests. Our experts not only test the attack surface between server and app, but also other critical components within apps.